Office 365 email setup for Thunderbird (Pop/IMAP – Modern Authentication)
T
Thunderbird is a free email application that’s easy to set up and customize – and it’s loaded with great features. Thunderbird will need to be updated to version 77.0.b1 or higher in order to work with Office 365. You can download the latest version of Thunderbird here.
Pre-requisites
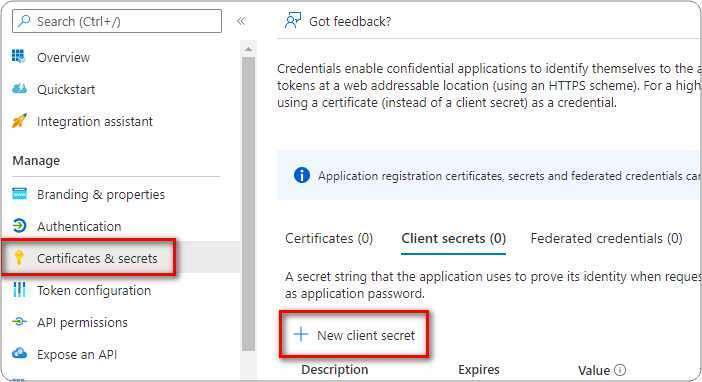
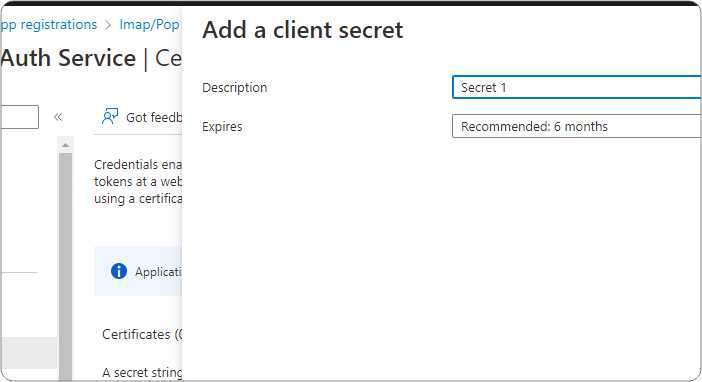
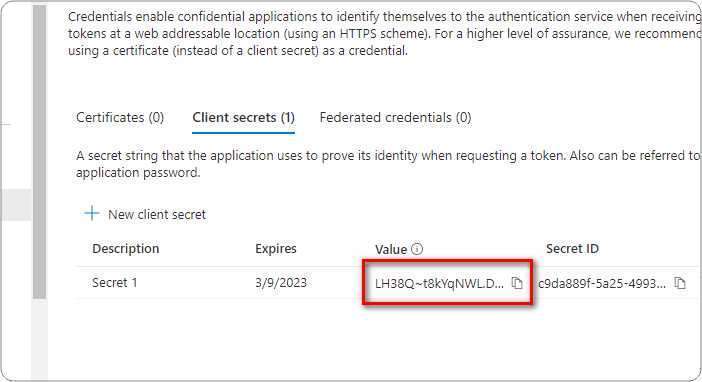
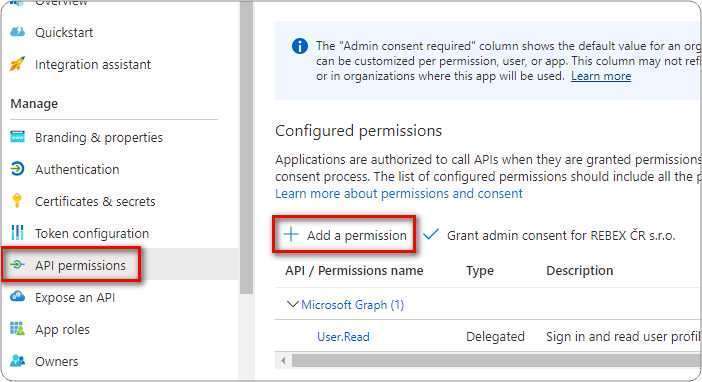
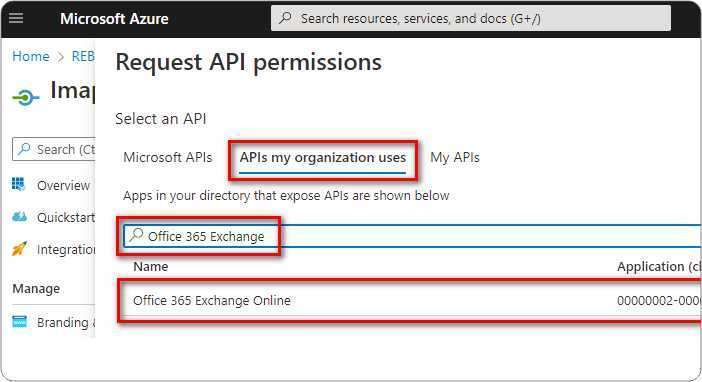
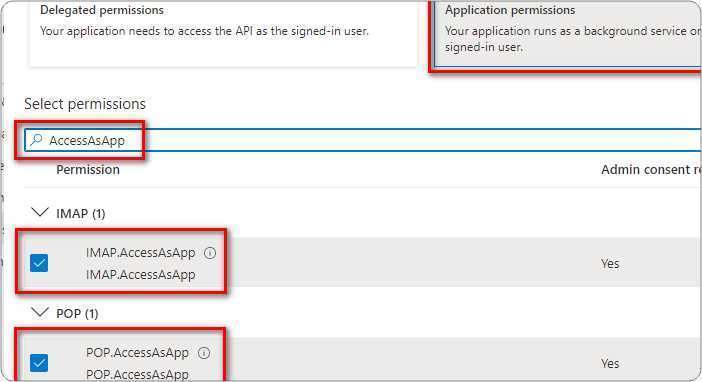
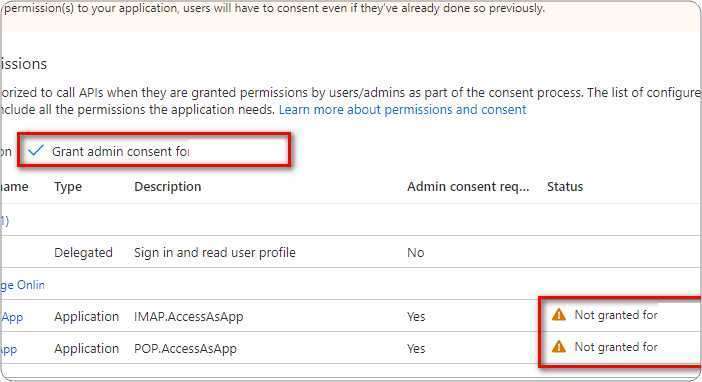
You need to ensure that you have already configured app registration in Azure Active Directory and granted users access to use the application. If not please follow steps in our earlier blog here.
Setting up Thunderbird
- Launch Thunderbird. Select +New, Existing Email Account from the ‘hamburger’ menu.
- Enter your name and e-mail address. You can leave the password empty. Press Continue to have Thunderbird figure out where your mailbox is hosted. This should discover your account in Office 365.
The settings you see should be:
Username: username@domain.com Password: Office 365 password Protocol: IMAP Incoming (IMAP): outlook.office365.com SSL Outgoing (SMTP): smtp.office365.com STARTTLS
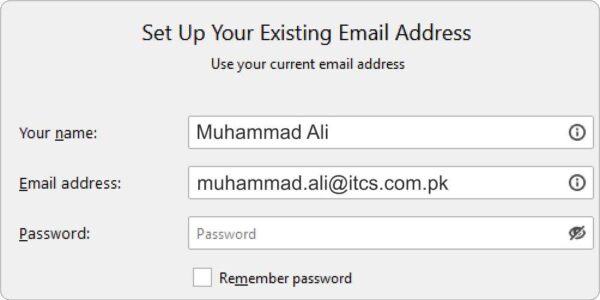
- Click Done to confirm the creation of your account. If you are prompted for your password, hit Cancel.
- Navigate to Account Settings -> Server Settings.
- Under Authentication method, select OAuth2.
- Navigate to Account Settings -> Outgoing Server.
- Under Authentication method, select OAuth2.
- Close the Account Settings. Select your Inbox, and you should be prompted with the Office 365 login page.
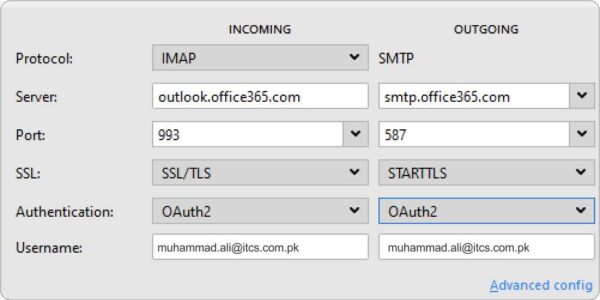
Manual Server Information
Username: username@domain.com Password: Office 365 password Incoming: IMAP Server: outlook.office365.com Port: 993 SSL Enabled: Yes Authentication: OAuth2 Outgoing: SMTP Server: smtp.office365.com Port: 587 SSL Enabled: STARTTLS Authentication: OAuth2